How We Helped a Manufacturing Client Avoid a Costly Data Breach (And What It Means for Your Business)
How We Helped a Manufacturing Client Avoid a Costly Data Breach (And What It Means for Your Business)
Most businesses only realize their cybersecurity gaps after something goes wrong. Fortunately, one of our mid-sized manufacturing clients didn’t have to learn that lesson the hard way.
They reached out to Alltech with a simple concern:
“We know our older antivirus system probably isn’t enough anymore, but we’re not sure where to begin—or how much risk we’re really facing.”
What followed was a real-world example of how proactive IT—delivered through a strategic partnership—can uncover silent threats, close security gaps, and provide lasting peace of mind.
Here’s how we helped them avoid a costly, reputation-damaging breach—and what you can take away if you’re wondering whether your current IT approach is keeping up with your growth.
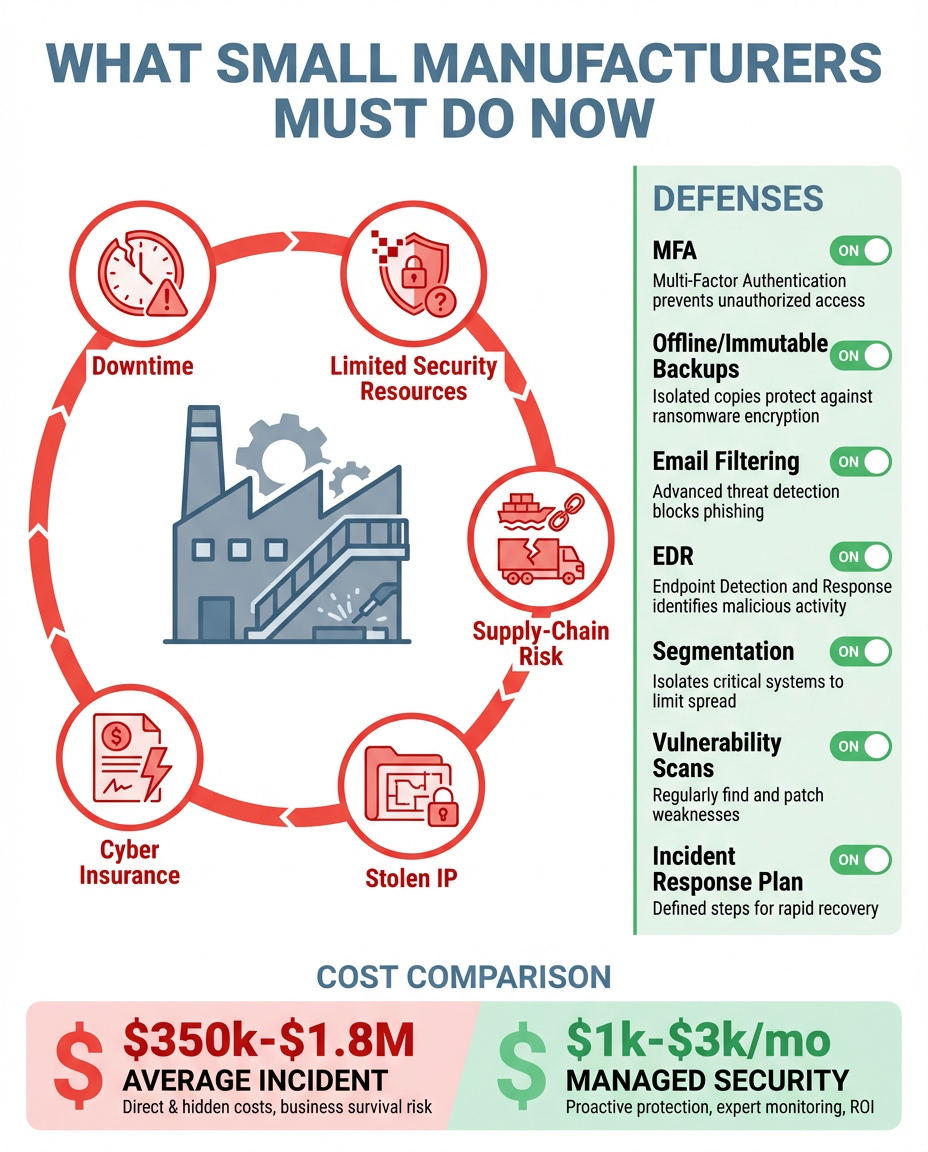
The Challenge: Flat-Footed Security in a Growing Company
Like many growing manufacturers, this client was focused on operations, fulfillment, and scaling output. IT was mostly reactive—springing into action when something broke or an employee clicked a suspicious link.
Their antivirus software was several years old. They assumed regular system scans meant they were protected. But zero-day threats, phishing emails, and ransomware are no match for basic antivirus in today’s threat landscape.
Employees were also storing sensitive customer specs, order sheets, and compliance documentation in unsecured shared folders—or worse, on local drives. That made data recovery difficult and opened the door to accidental data loss or exposure during a breach.
They didn’t know what they didn’t know—and that’s where most risk hides.
Our Solution: Full-Stack Protection with Strategic Oversight
Once engaged through our managed services model, we started with a baseline audit. Within days of deploying our Alltech Endpoint Pro Suite—powered by Kaseya—we detected:
- Active phishing attempts targeting company email domains
- Multiple outdated systems lacking critical security patches
- Privileged accounts with no multi-factor authentication
- Unmonitored endpoints vulnerable to ransomware
With their team’s trust, we didn’t just patch and run. We built a long-term protection roadmap that aligned with their business goals, industry regulations, and internal workflows.
Here’s what our approach looked like in action:
1. Threat Detection and Response
Our Alltech Endpoint Pro Suite provided real-time monitoring and automated response to threats across all servers and workstations. We also configured alerting and rollback features that gave our client visibility and immediate remediation capabilities.
2. Managed Security Operations
With our team overseeing updates, configurations, and endpoint health, their leadership no longer had to guess whether systems were secure. We became their outsourced—but fully embedded—security team.
3. User Education and Phishing Simulation
We upgraded their user awareness through our Alltech User Protection Suite—powered by Kaseya. Phishing simulations and training helped their team spot scams and unsafe behavior before clicks became compromises.
4. File Safety and Governance
We implemented Alltech Secure File Share—powered by Egnyte to give employees a secure, compliant way to collaborate and store heavy CAD files and sensitive documents.
The Outcome: Problems Solved Before They Hurt the Business
Had these vulnerabilities gone undetected, it was only a matter of time before something was compromised—whether that meant ransomware locking down production files, customer data exposed, or compliance fines stacking up.
Instead, this client got in front of the risk—without needing to rip and replace their entire tech stack. We layered in tools, training, and support that matched their growth stage and maturity level, giving them protection and room to scale confidently.
Most importantly—they no longer feel like cybersecurity is “someone else’s problem” or a box to check. It’s now a strategic asset built into their operations.
Does This Sound Familiar? You Might Be Ready for Proactive IT
We’ve seen it over and over: business owners feel growing concern about cybersecurity—but don’t want to overcorrect or chase every headline.
That’s why our approach is all about education, alignment, and action—not upselling or overwhelming. We work alongside leadership teams to integrate smarter, scalable protection into everyday business.
Because when IT systems work together, stay monitored, and evolve with your needs, threats don’t become disasters.
Let’s Talk: What Risks Are Hiding in Your Network?
If your business has grown, but your IT strategy hasn’t... you might be more exposed than you realize. The good news? A strategic partnership with a partner like Alltech can flip security from a worry into a strength.
Let’s talk—visit alltechsupport.com , call 205-290-0215, or email sales@alltechsupport.com .
Ask us to walk you through our initial audit steps, explore how our proactive services work, or share a copy of the in-depth client case study featured here.
We’re here to help you protect what you’ve built—and prepare for what’s next.