Securing the Production Line: A Strategic Framework for Manufacturing Cybersecurity Excellence
Securing the Production Line: A Strategic Framework for Manufacturing Cybersecurity Excellence
Manufacturing operations face an unprecedented convergence of cyber and physical risk. Recent data from IBM's 2024 X-Force Threat Intelligence Index reveals that manufacturing ranks as the second most targeted industry, experiencing a 40% increase in cyberattacks year-over-year (IBM Security). The stakes have never been higher: a successful breach can halt production lines, compromise product integrity, and create cascading supply chain disruptions that reverberate across entire industries.
Critical manufacturing operations exist at the intersection of operational technology (OT) and information technology (IT)—a convergence that creates both opportunity and vulnerability. Legacy industrial control systems, designed for reliability rather than security, now connect to enterprise networks and cloud platforms. This digital transformation unlocks efficiency gains but exposes critical infrastructure to sophisticated threat actors who understand exactly how to weaponize these connections.
The question facing manufacturing leaders isn't whether an attack will occur, but whether their organization will be prepared to detect, contain, and recover when it does.
The Manufacturing Threat Landscape: Why Now Demands Action
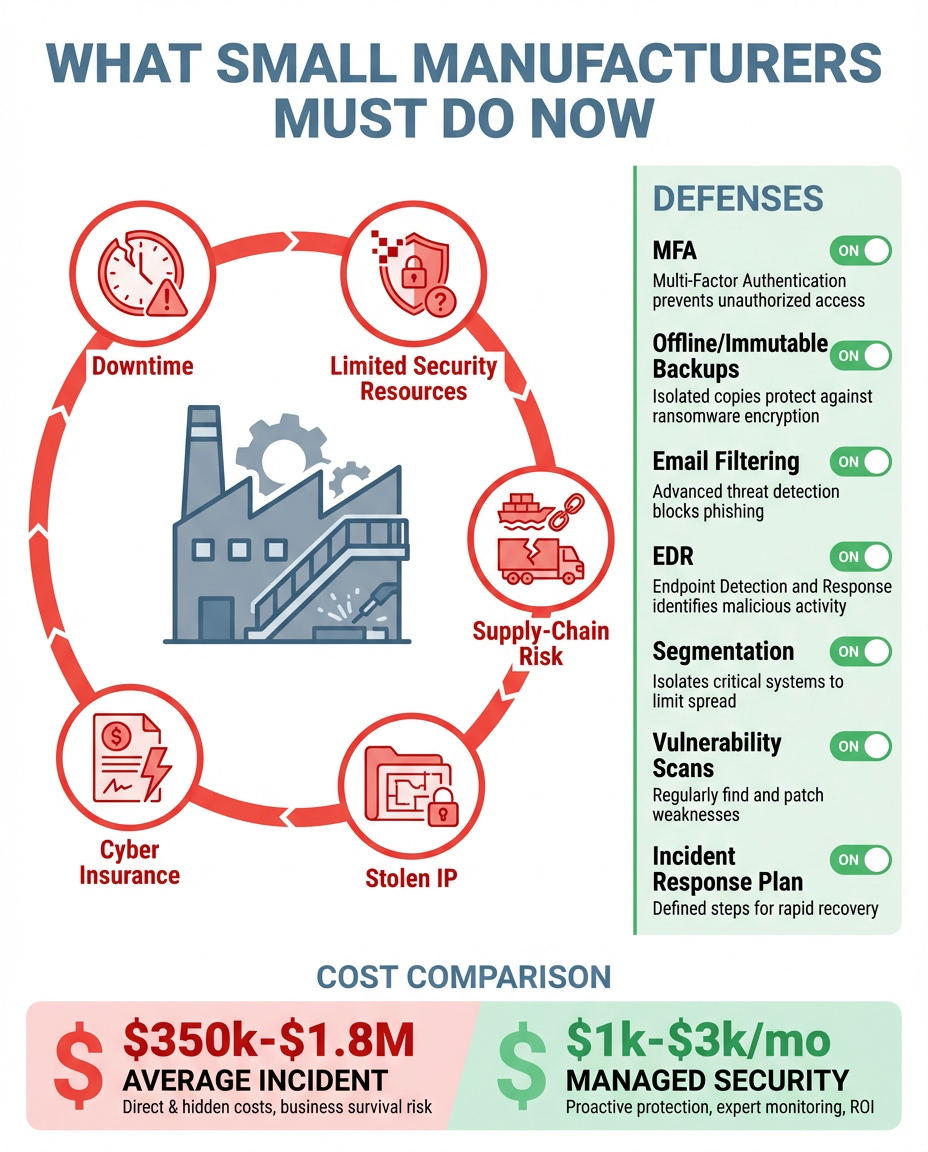
Manufacturing cybersecurity has evolved far beyond protecting office computers. Today's threats target the heart of production: programmable logic controllers (PLCs), human-machine interfaces (HMIs), and industrial IoT devices that control everything from assembly lines to safety systems. The Cybersecurity and Infrastructure Security Agency (CISA) recently issued new guidance specifically addressing these vulnerabilities, emphasizing that "manufacturing environments face unique challenges due to the integration of IT and OT systems" (CISA Cross-Sector Cybersecurity Performance Goals).
Three critical factors drive the urgency:
- Expanding Attack Surface: Every connected sensor, every cloud integration, and every remote access point creates a potential entry vector. Modern manufacturing facilities contain thousands of networked devices, many lacking basic security controls or regular updates.
- Economic Impact Amplification: Manufacturing downtime costs have skyrocketed. A single day of production stoppage can cost large manufacturers millions in lost revenue, missed delivery commitments, and customer confidence. When attackers successfully infiltrate industrial networks, they often target multiple systems simultaneously to maximize disruption.
- Supply Chain Interdependence: Manufacturing operations don't exist in isolation. A cybersecurity incident at one facility can trigger shortages, quality issues, and delivery delays that affect dozens of downstream customers and suppliers.
The Anatomy of Manufacturing Cyber Threats
Understanding how attackers target manufacturing requires examining both their methods and motivations. Unlike opportunistic cybercriminals seeking quick financial gain, threat actors targeting manufacturing often pursue strategic objectives: intellectual property theft, competitive intelligence, or operational disruption.
- Ransomware Evolution: Modern ransomware groups study manufacturing environments before deploying attacks. They identify critical production windows, understand which systems control safety mechanisms, and time their attacks for maximum pressure. Some groups now threaten to publish stolen intellectual property alongside traditional data encryption, creating dual pressure points for ransom payment.
- Supply Chain Infiltration: Attackers increasingly target smaller suppliers and vendors as stepping stones into larger manufacturing networks. These organizations often lack robust cybersecurity controls but maintain privileged access to their customers' systems for logistics, quality monitoring, or maintenance activities.
- Industrial IoT Exploitation: Connected manufacturing equipment frequently ships with default passwords, unencrypted communications, and limited update mechanisms. Attackers exploit these weaknesses to establish persistent footholds within industrial networks, sometimes remaining undetected for months while gathering intelligence or positioning for future attacks.
- Insider Threat Amplification: Manufacturing environments create unique insider risk scenarios. Disgruntled employees with physical access to production systems can cause immediate operational damage, while compromised credentials allow external attackers to blend normal maintenance activities with malicious actions.
Architecting Manufacturing Cybersecurity: The AllTech Strategic Framework
Effective manufacturing cybersecurity requires an integrated approach that addresses both digital and physical risk vectors. Our framework recognizes that manufacturing security isn't simply about deploying more technology—it's about creating resilient systems that maintain production continuity while adapting to evolving threats.
Foundation Layer: Visibility and Asset Intelligence
Manufacturing cybersecurity begins with comprehensive asset visibility. Our AllTech Lifecycle Asset Intelligence service discovers, catalogs, and continuously monitors every connected device across IT and OT environments. This foundation identifies vulnerable legacy systems, tracks firmware versions, and maintains real-time inventory of critical production assets. Traditional network scanning tools often fail in manufacturing environments due to the sensitivity of industrial protocols and the diversity of connected devices. Our platform uses passive monitoring techniques that provide complete visibility without disrupting production operations.
Protection Layer: Multi-Vector Defense
Manufacturing networks require defense strategies that account for both sophisticated external threats and potential insider risks. Our AllTech Endpoint Pro Suite deploys behavioral analysis and machine learning algorithms specifically tuned for industrial environments. Unlike consumer-focused security tools, our solution understands normal patterns in manufacturing networks and can distinguish between legitimate operational changes and potential security incidents.
The AllTech User Protection Suite addresses the human element through continuous security awareness training tailored to manufacturing roles. Production floor workers, maintenance technicians, and engineering staff each face unique threat scenarios requiring specialized training approaches.
Detection Layer: Continuous Monitoring and Threat Intelligence
Manufacturing cyberattacks often unfold over extended periods, with attackers conducting reconnaissance, establishing persistence, and carefully planning their approach. Our 24/7 Security Operations Center (SOC) maintains specialized expertise in manufacturing threat patterns and industrial protocol analysis.
Real-time monitoring extends beyond network traffic to include analysis of production data patterns, equipment behavior anomalies, and integration with existing manufacturing execution systems (MES) and supervisory control and data acquisition (SCADA) platforms.
Response Layer: Incident Containment and Business Continuity
When security incidents occur in manufacturing environments, response time directly correlates with production impact. Our AllTech Business Continuity Suite ensures that critical systems can be rapidly restored while forensic analysis proceeds in parallel.
Incident response procedures account for the unique requirements of manufacturing operations: maintaining safety system integrity, preserving production data, and coordinating with regulatory authorities when required.
Governance Layer: Compliance and Risk Management
Manufacturing organizations face complex regulatory requirements spanning cybersecurity, safety, and quality standards. Our AllTech Compliance Manager automates evidence collection, maintains audit trails, and provides continuous assessment against frameworks including NIST Manufacturing Profile, ISO 27001, and industry-specific requirements.
The Tangible Business Outcomes
Manufacturing cybersecurity investments deliver measurable value across four critical dimensions:
Operational Resilience: Organizations implementing comprehensive cybersecurity frameworks report 60% fewer unplanned production interruptions. When incidents do occur, response times improve dramatically—from hours or days to minutes—minimizing production impact and customer delivery disruptions.
Intellectual Property Protection: Manufacturing companies invest millions in research, development, and process optimization. Robust cybersecurity controls protect these competitive advantages from theft while enabling secure collaboration with suppliers, customers, and research partners.
Regulatory Confidence: Manufacturing operations increasingly face cybersecurity compliance requirements from customers, insurers, and regulatory bodies. Proactive security posture reduces audit burdens, accelerates customer qualification processes, and supports favorable cyber insurance terms.
Strategic Competitive Advantage: Manufacturers with strong cybersecurity capabilities can confidently pursue digital transformation initiatives—IoT deployments, cloud integration, and advanced analytics—that create operational efficiencies and new business opportunities.
Implementation Roadmap: Your Strategic Next Step
Manufacturing cybersecurity maturity develops through deliberate, phased implementation that balances security improvements with operational continuity. Our recommended approach prioritizes quick wins while building toward comprehensive coverage:
- Phase 1: Foundation and Visibility (30-60 days)
Deploy asset discovery and continuous monitoring across critical production systems. Establish baseline security controls and implement basic access management for industrial networks. - Phase 2: Protection and Training (60-120 days)
Implement endpoint protection tuned for manufacturing environments and deploy security awareness training programs. Establish incident response procedures and communication protocols. - Phase 3: Advanced Detection and Integration (120-180 days)
Deploy behavioral analytics and threat intelligence capabilities. Integrate security monitoring with existing manufacturing systems and establish automated response capabilities. - Phase 4: Optimization and Expansion (180+ days)
Extend security controls to supplier networks and remote facilities. Implement advanced compliance automation and continuous risk assessment capabilities.
Manufacturing cybersecurity isn't a destination—it's an ongoing strategic capability that evolves with your operations and the threat landscape. The organizations that begin this journey today position themselves for sustained competitive advantage in an increasingly connected manufacturing ecosystem.
About AllTech IT Solutions
AllTech is a leading provider of integrated IT management and cybersecurity solutions. We partner with businesses to transform their technology from a liability into a strategic asset, delivering robust security, operational efficiency, and a clear path to compliance. Our expert team leverages best-in-class platforms to build proactive and resilient technology environments.
Take the Next Step
Ready to fortify your defenses and turn your security posture into a competitive advantage? See how AllTech's strategic approach can be tailored to your unique business challenges.
Contact our cybersecurity strategists today for a complimentary security consultation.
Email: Sales@AllTechSupport.com
Phone: 205-290-0215
Web: AllTechSupport.com
Works Cited
CISA. "Cross-Sector Cybersecurity Performance Goals." Cybersecurity and Infrastructure Security Agency, 2024, www.cisa.gov/cross-sector-cybersecurity-performance-goals.
IBM Security. "X-Force Threat Intelligence Index 2024." IBM Corporation, 2024, www.ibm.com/security/data-breach/threat-intelligence/.