Complete IT Security & Support
Complete IT Security & Support
Protecting Your Business from Every Angle
The Reality Every Business Faces
Your business runs on technology. But with that convenience comes constant risk:
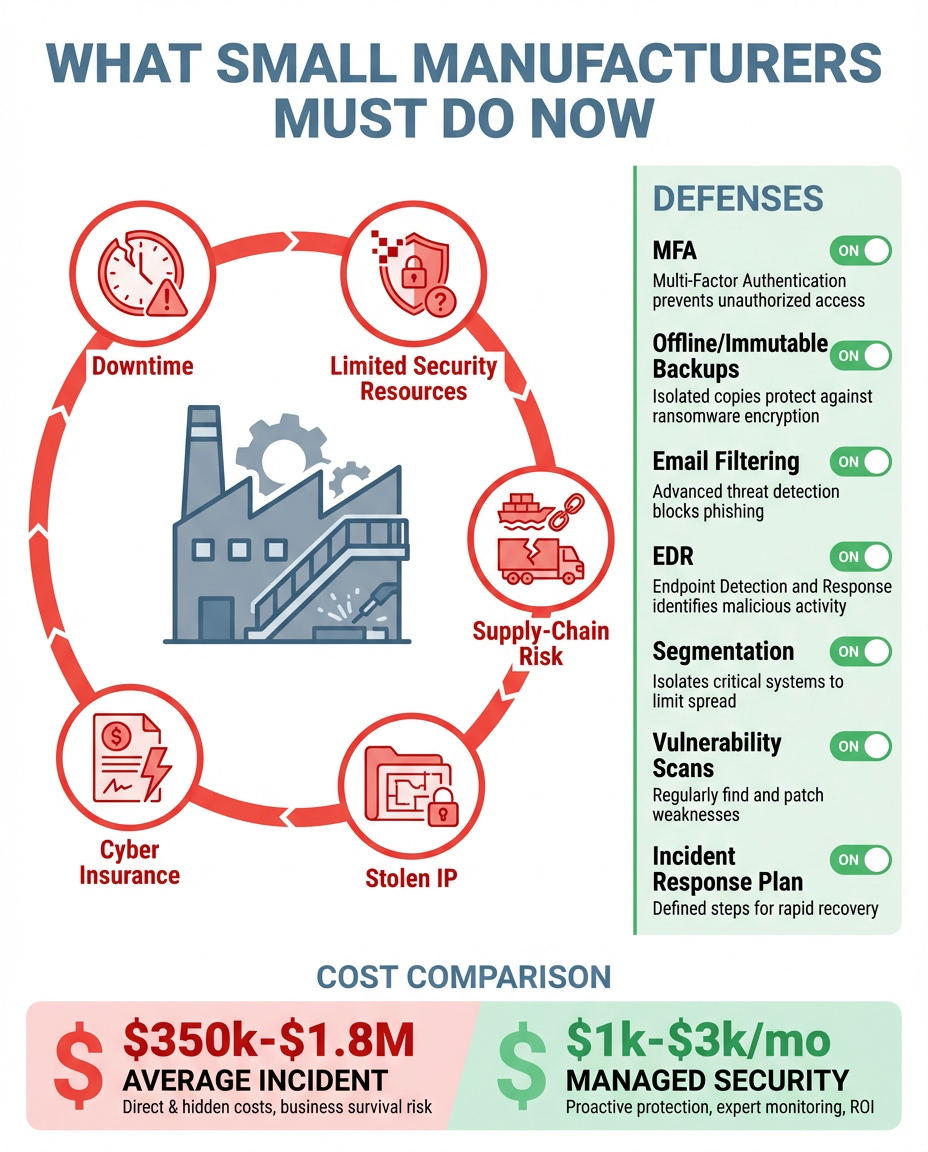
- One wrong click on a phishing email can compromise your entire network
- Unpatched devices create doorways for ransomware attacks
- Stolen credentials from data breaches give attackers easy access
- Outdated systems slow your team down and create security gaps
- Cloud applications expand your attack surface without you realizing it
- When disaster strikes, can you recover your critical data?
The bottom line: Your employees are working harder than ever, your IT environment is more complex, and cyber threats are becoming more sophisticated every single day.
You need protection that works 24/7—without adding complexity to your team's day.
How AllTech Solves These Problems
At AllTech IT Solutions, we protect your business from two critical angles: securing your people and securing your technology. Our fully managed services work together seamlessly, creating multiple layers of defense that keep your business running safely and efficiently.
Protecting Your Team: User Protection & Enablement Services
The Problem: Your employees are the #1 target—and they don't know it.
Cybercriminals know that humans are often the weakest link. Sophisticated phishing attacks, credential theft, and social engineering tactics are designed specifically to trick your staff—and traditional antivirus software won't stop them.
Our Solution: We transform your team into a human firewall.
Security Awareness & Phishing Training
- Monthly interactive training that's short, relevant, and actually engaging
- Realistic phishing simulations sent directly to inboxes to test awareness
- Progress tracking by individual and department—see who's improving
- Industry-specific paths for HIPAA, PCI, or cyber insurance requirements
- Year-over-year audit records ready for compliance reviews
Credential Exposure & Dark Web Monitoring
- 24/7 scanning of criminal marketplaces and breach databases
- Instant alerts when employee credentials appear in breaches
- Immediate action: Password resets, MFA enforcement, account lockouts
- Executive reporting showing your organization's exposure level
- Protection extends to vendors, executives, and critical accounts
Advanced Email & Account Security
- Real-time warning banners appear in every email inbox
- "External Sender" alerts prevent spoofing and impersonation
- Red flags for suspicious links, attachments, and domain mismatches
- Context-aware protection that adjusts based on threat level
- Seamless integration with Microsoft 365 and Google Workspace
Cloud App Behavior Monitoring & Automated Response
Your team uses cloud tools like Microsoft 365, Google Workspace, Dropbox, and Slack every day. But unusual activity can signal a compromised account or insider threat.
We watch for:
- Mass file downloads or deletions
- Logins from unusual locations or multiple regions
- Sensitive files shared outside your organization
- Unauthorized third-party app usage
- Access to confidential data at odd hours
- Failed logins followed by successful access
We automatically respond by:
- Locking compromised accounts
- Terminating suspicious sessions
- Revoking file sharing rights
- Requiring password resets or MFA
- Blocking risky downloads or app usage
- Alerting your IT team immediately
Protecting Your Technology: Endpoint Protection & Automation Services
The Problem: Every device is a potential entry point for attackers.
Desktops, laptops, remote workstations—each one needs to be patched, monitored, backed up, and secured. Miss just one, and you've left the door wide open. Managing this manually is impossible, especially with hybrid and remote work.
Our Solution: Every endpoint is monitored, maintained, and secured 24/7.
Device Monitoring, Maintenance & Support
- 24/7 real-time monitoring of every device's health and performance
- Automated patching for operating systems and over 200 applications
- Remote issue resolution —our technicians fix problems without delays
- On-site service included when hands-on support is needed
- Proactive alerts identify hardware failures before they happen
- Asset tracking and device lifecycle reporting
- Policy enforcement applied consistently across all endpoints
Threat Detection & Response (MDR)
- AI-powered behavioral analysis detects ransomware and zero-day exploits
- 24/7 Security Operations Center (SOC) monitoring every threat
- Immediate response to active attacks with expert escalation
- Real-time quarantine of threats before they spread
- Security policies enforced based on user role, location, and device risk
- Compliance-ready logging for audits and reporting
Backup & Recovery for Endpoints
- Daily encrypted backups of critical files and system data
- Cloud-based storage with secure retention policies
- Rapid file restore or full system recovery options
- Ransomware rollback capabilities get you back online fast
- Protection from data loss, corruption, or device failure
Note: Backup services may incur additional costs based on cloud storage usage (billed in 1TB increments).
IT Automation & Efficiency
- Automated patching supports HIPAA, NIST, PCI, and cyber insurance compliance
- Device onboarding/offboarding workflows save time and reduce errors
- Self-healing policies fix common issues automatically (disk space, crashed services, etc.)
- Scheduled maintenance happens during off-hours
- Unified policy enforcement ensures consistency across your network
Complete Visibility & Reporting
We deliver scheduled and on-demand reports that show exactly how we're protecting you:
User Protection Reporting:
- Credential exposure history and remediation logs
- Phishing simulation results by user and department
- Cloud behavior insights and policy violations
- Monthly threat summaries and email activity
Endpoint Protection Reporting:
- Patch status and compliance tracking
- System uptime and performance trends
- Security alerts and threat response logs
- Device inventory and warranty status
- Backup verification and restore activity
Why AllTech's Comprehensive Approach Works
Cybersecurity isn't just an IT issue—it's a people issue AND a technology issue.
Most security solutions focus on one or the other. AllTech protects both:
- Your people are trained, monitored, and empowered to make smart security decisions
- Your devices are patched, protected, and automatically defended against threats
- Your cloud environment is monitored and secured with intelligent automation
- Your data is backed up and recoverable when you need it
- Your compliance needs are supported with audit-ready documentation
Everything is fully managed. Always on. Built for businesses that can't afford downtime or breaches.
The Bottom Line
You get:
- Fewer security incidents because threats are stopped early
- Less downtime because problems are fixed proactively
- Stronger compliance with automated documentation and policies
- Better insurance rates with proven security training and monitoring
- Peace of mind knowing experts are watching 24/7
Your team can focus on growing your business—not worrying about IT security.
Ready to Protect Your Business?
AllTech IT Solutions
300 Century Park South, Suite 200
Birmingham, Alabama 35226
Phone: 205.290.0215
Fax: 205.290.0276