The Complete Guide to IT Compliance for Automotive Dealerships: FTC Safeguards Rule, PCI DSS, and CCPA Requirements in 2025
Look, I'm not going to sugarcoat this. If you're running an automotive dealership in 2025, you're dealing with the most complicated compliance mess the industry has ever seen. We're talking FTC Safeguards Rule, PCI DSS 4.0.1, California's increasingly aggressive CCPA enforcement... and let's not forget those recent breaches that hit thousands of dealers. At this point, the question isn't really whether you should prioritize IT compliance. It's whether you can afford NOT to.
Here's something most vendors won't mention upfront (because, well, they want your business): the average dealership is looking at upfront compliance costs around $293,975, plus annual ongoing costs of about $276,925. Yeah, I know. That's according to NADA's analysis, and those numbers don't even include the potential penalties, which can hit $51,744 per violation under federal law. Daily fines? They can reach $50,120 (Federal Trade Commission).
This guide covers everything you need to know about your compliance obligations, how to avoid those devastating penalties, and what you can do to protect your dealership from the ransomware attacks that cost the industry over $600 million in 2024 alone (CDK Global). Let's dive in.
What IT Regulations Apply to Automotive Dealerships?
So here's the thing... automotive dealerships operate under this unique regulatory framework where you're basically treated as financial institutions when it comes to data security. Kind of makes sense when you think about it, right? You're handling financing, credit applications, all that sensitive stuff. Here are the four main regulations you've got to deal with:
1. FTC Safeguards Rule (Gramm-Leach-Bliley Act)
Who it applies to: Pretty much every dealership that finances or leases vehicles. So yeah, that's virtually all franchised dealers and most independent ones too.
Why it matters: The FTC considers you a "financial institution" because you facilitate financing. I know, you probably think of yourself as a car dealer, not a bank... but legally speaking, you're subject to the same data security standards as actual banks.
Full compliance deadline: June 9, 2023 (which has already passed, meaning you should technically already be compliant. If you're not, well... we need to fix that.)
The FTC Safeguards Rule requires eleven specific security measures. Let me break these down:
- Designate someone qualified to oversee your information security program (this can't just be Jim from accounting who "knows computers")
- Conduct written risk assessments of your operations
- Create and maintain a complete inventory of all your data and systems
- Encrypt ALL customer data, both at rest and in transit
- Implement multi-factor authentication on all systems with customer information
- Conduct annual penetration testing by qualified personnel
- Perform biannual vulnerability assessments (that's twice a year)
- Evaluate and document your service providers' security capabilities
- Provide security awareness training to all employees
- Create and test an incident response plan
- Report breaches affecting 500 or more consumers to the FTC within 30 days
The cost of non-compliance: Individual violations carry penalties of $51,744, and that number gets adjusted annually for inflation. Companies can face fines of $100,000 per violation. Here's where it gets really interesting... corporate officers can be personally liable for up to $10,000 per violation. Daily fines can reach $50,120 per occurrence (Federal Trade Commission). So yeah, this isn't something you want to ignore.
2. PCI Data Security Standard (PCI DSS) 4.0.1
Who it applies to: Any dealership that processes, stores, or transmits credit card information. Which is, let's be honest, probably you.
Full compliance deadline: March 31, 2025 (that's coming up fast, by the way)
PCI DSS 4.0.1 is a significant update from version 3.2.1, which expired back on March 31, 2024. The standard requires six core security objectives:
- Build and maintain secure networks and systems
- Protect cardholder data through encryption and tokenization
- Maintain a vulnerability management program
- Implement strong access control measures
- Regularly monitor and test networks
- Maintain a comprehensive information security policy
The cost of non-compliance: The card brands (Visa, Mastercard, American Express, Discover) can impose some pretty hefty fines, increase your processing fees, or even revoke your ability to accept credit cards altogether. Remember Target's data breach? That resulted in an $18.5 million settlement. That's the kind of cautionary tale that should keep you up at night if you're handling payment card data (PCI Security Standards Council).
3. California Consumer Privacy Act (CCPA) and California Privacy Rights Act (CPRA)
Who it applies to: Dealerships operating in California that collect consumer personal information.
Why California matters nationally: Okay, so even if you're not in California, pay attention here. California's regulations have this tendency to become de facto national standards. And the California Privacy Protection Agency (CPPA)? They're not messing around with enforcement.
Here's a perfect example: On March 12, 2025, Honda Motor Company paid $632,500 to settle CCPA violations. What did they do wrong? They required excessive verification for privacy rights requests, used asymmetric privacy tools, blocked authorized agents, and maintained inadequate advertising technology contracts (California Privacy Protection Agency). So yeah, they're serious.
Key CCPA/CPRA requirements for dealerships:
- Display a "Do Not Sell or Share" link on every webpage that collects personal information
- Provide clear privacy notices explaining what data you collect and how you use it
- Honor consumer requests for data access, deletion, and opt-out within specified timeframes
- Implement cookie consent mechanisms
- Support Global Privacy Control (GPC) signals
- Maintain compliant contracts with third-party service providers
Penalties: Up to $2,500 per unintentional violation and $7,500 per intentional violation. Now multiply that by hundreds or thousands of consumer records... the math gets ugly fast (California Privacy Protection Agency).
Coming soon: By 2027, California dealerships will need to comply with new Automated Decision-Making Technology (ADMT) rules and implement formal risk assessment processes. Fun times ahead.
4. FinCEN Form 8300 Reporting
Who it applies to: All dealerships receiving cash payments exceeding $10,000.
The Financial Crimes Enforcement Network (FinCEN) requires businesses to report cash transactions over $10,000 within 15 days using Form 8300. This is an anti-money laundering requirement, and it carries some seriously criminal penalties for non-compliance.
Real consequences: One auto dealer was sentenced to three years in prison and forfeited $85,000 for evading Form 8300 requirements (Financial Crimes Enforcement Network). So yeah, don't mess with this one.
What Does Compliance Actually Look Like? The Practical Requirements
Alright, let's translate all that regulatory jargon into actual actions you need to take.
Data Security Infrastructure
Encryption requirements:
- All devices containing customer information must use full-disk encryption (BitLocker for Windows, FileVault for Mac)
- Email transmission of sensitive data requires TLS encryption
- If you absolutely must email sensitive attachments, use password-protected ZIP files (though honestly, there are better ways to do this)
- All data moving between systems must be encrypted
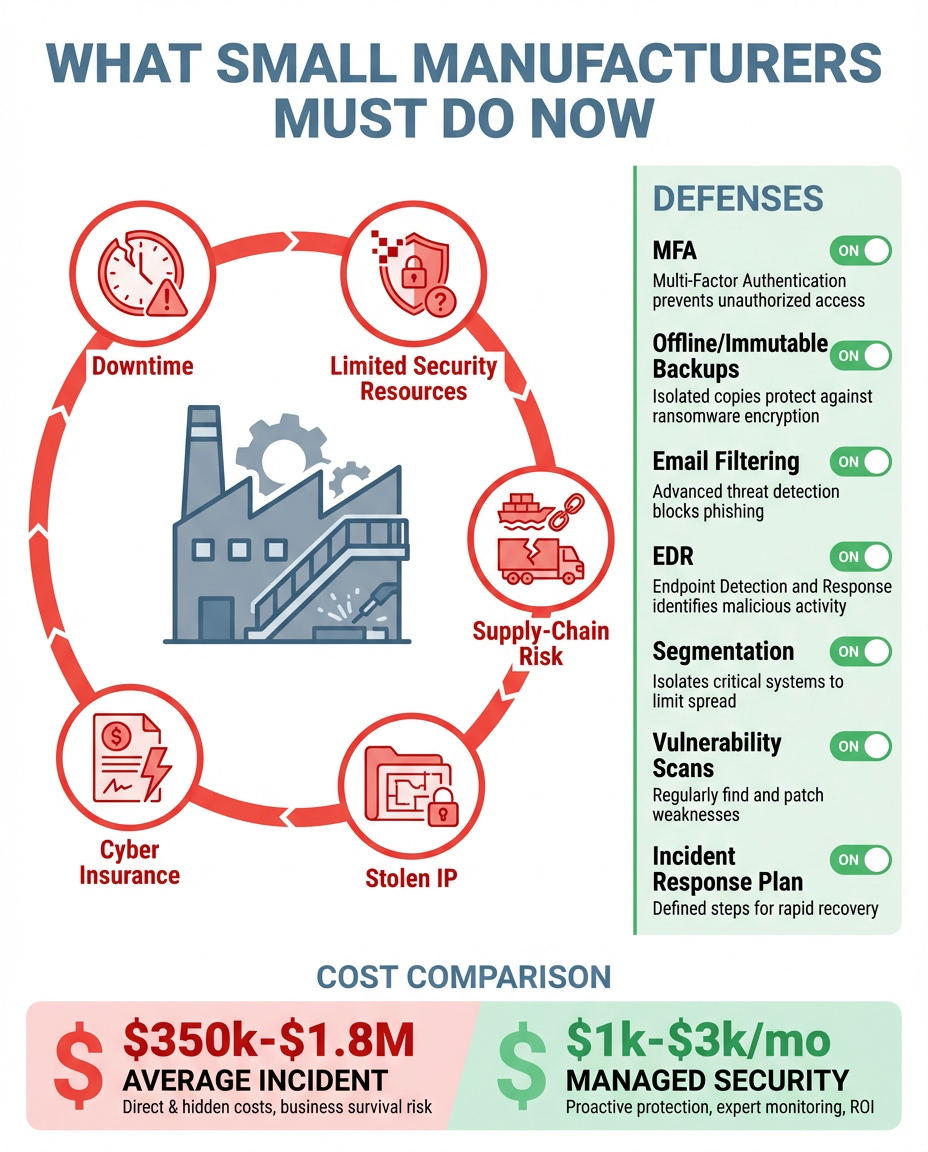
Multi-factor authentication (MFA):
You need MFA on:
- Dealer Management Systems (DMS)
- Customer Relationship Management (CRM) platforms
- Credit reporting and compliance systems
- Email accounts with access to customer data
- Remote access to your dealership network
- Any web-based application containing customer information
Popular MFA solutions include Okta, Duo Security, Microsoft 365 native MFA, and Azure Active Directory. Pick one and implement it... like yesterday.
Risk Assessment and Testing
Annual penetration testing:
You've got to conduct annual penetration tests that include:
- Phishing and social engineering simulations
- Ransomware emulation exercises
- Password cracking attempts
- Web application security testing
- Active Directory security assessment
- Network vulnerability scanning
Biannual vulnerability assessments:
Every six months, you need to scan your systems for vulnerabilities. You can use automated scanning tools or manual assessments by qualified professionals.
Why this matters: Look at what happened to the automotive industry in 2024. The CDK Global breach affected over 15,000 dealerships and cost the industry an estimated $600 million in lost operations (CDK Global). Annual testing helps you find vulnerabilities before the bad guys do.
Vendor Management: Your Weakest Link
Here's an uncomfortable truth that nobody really wants to talk about: your vendors might be your biggest security risk. The 2024-2025 700Credit breach affected 18,000 dealerships and 5.6 million customers. Not because those dealerships had weak security... but because their vendor did (Federal Trade Commission). Think about that for a second.
Required vendor management steps:
1. Inventory all service providers with access to customer information. I'm talking about:
- DMS providers (CDK, Reynolds & Reynolds, Dealertrack)
- CRM platforms (VinSolutions, DealerSocket, Elead)
- Credit reporting services (700Credit, Dealertrack Credit, RouteOne)
- Payment processors
- Website providers
- Email and communication tools
- Data analytics providers
- Cloud storage services
- Your IT managed service provider
2. Assess vendor security capabilities by:
- Reviewing SOC 2 reports
- Distributing security questionnaires
- Examining vendor security certifications
- Evaluating vendor incident response capabilities
3. Require contractual security commitments that specify:
- Data encryption requirements
- Access control measures
- Breach notification timelines
- Data deletion procedures when the contract ends
- Right to audit vendor security practices
4. Periodically reassess vendor security through annual reviews
Employee Training: Your Human Firewall
Get this: phishing emails cause 90% of ransomware incidents in the automotive industry (CrowdStrike). Your employees are both your greatest vulnerability AND your strongest defense. It's a bit paradoxical, but there you have it.
Required training components:
- Initial security awareness training for all new hires
- Annual refresher training for all employees (yes, all of them)
- Specialized training for IT staff and anyone with elevated system access
- Regular phishing simulation exercises (these are actually kind of fun to watch, in a morbid way)
- Proper handling procedures for sensitive customer information
- Incident reporting protocols
Document everything: Keep records showing who completed training and when. This documentation becomes part of your "Book of Evidence" that demonstrates compliance. Trust me, you'll want this if you ever get audited.
Incident Response: Planning for the Inevitable
You need to create, document, and test a written incident response plan. Notice I said "when," not "if"... because in today's environment, it's really just a matter of time. Your plan should include:
- Defined roles and responsibilities for incident response team members
- Step-by-step remediation procedures for different incident types
- Communication protocols for notifying affected parties
- Documentation requirements for post-incident analysis
- Procedures for reporting breaches to the FTC within 30 days (for breaches affecting 500+ consumers)
Critical requirement: Conduct annual tabletop exercises where your team practices responding to simulated security incidents. These exercises help you identify gaps in your plan before a real emergency happens. And believe me, you do NOT want to be figuring this stuff out in the middle of an actual crisis.
What If You're a Small Dealer? Are There Exemptions?
The FTC Safeguards Rule does include limited exemptions for dealerships serving fewer than 5,000 consumers. If you qualify, you're not required to:
- Produce written risk assessments
- Create written incident response plans
- Submit written annual reports
- Conduct continuous monitoring, penetration testing, or vulnerability scans
However—and this is a big however—most dealerships won't qualify for this exemption. If your dealership sells or leases even 100 vehicles per year, you'll likely exceed the 5,000-consumer threshold within a few years when you count service customers, parts customers, and all those people who submitted credit applications but didn't end up buying.
Even if you technically qualify for the exemption, implementing these security measures is still best practice for protecting your business from devastating cyberattacks. I mean, why take the risk?
What Are the Real-World Costs of Compliance?
Let's talk money. I'm going to be transparent about costs here, because another vendor might try to downplay these numbers, but you deserve the truth.
According to NADA's analysis, the average dealership is looking at:
- Upfront costs: $293,975
- Annual ongoing costs: $276,925
These estimates include stuff like:
- Purchasing and implementing encryption and MFA solutions
- Conducting penetration tests and vulnerability assessments
- Upgrading network infrastructure
- Hiring or contracting qualified security personnel
- Training employees
- Updating vendor contracts
- Documenting policies and procedures
- Maintaining compliance management systems
Cost variables that affect your specific situation:
- Your current security posture (starting from scratch costs way more than updating existing measures)
- Number of locations
- Amount of customer information you're storing
- Number of employees requiring training
- Complexity of your vendor ecosystem
- Whether you use a Managed Security Service Provider (MSSP)
The cost of non-compliance is actually higher: Think about it... a single FTC violation at $51,744, multiplied across multiple deficiencies, plus the reputational damage of a data breach, plus potential civil lawsuits from affected customers, plus operational disruption. When you run the math, it strongly favors proactive compliance.
What Should You Do Right Now?
Here's a prioritized action plan to get you started:
Immediate actions (do these this week):
- Appoint someone qualified as your Information Security Program coordinator
- Conduct a gap analysis comparing your current practices against FTC Safeguards Rule requirements
- Inventory all systems and databases containing customer information
- Enable MFA on all systems with customer data (start with DMS and email)
- Review your website for CCPA compliance, especially those "Do Not Sell or Share" links
Short-term actions (get these done this month):
- Enable encryption on all devices storing customer information
- Create an inventory of all vendors with customer information access
- Schedule your first penetration test and vulnerability assessment
- Review and update vendor contracts to include security requirements
- Start documenting your written Information Security Program
Medium-term actions (tackle these this quarter):
- Implement a comprehensive security awareness training program
- Conduct phishing simulation exercises
- Create and document your incident response plan
- Verify PCI DSS compliance with your payment processor
- Establish procedures for FTC breach notification
Ongoing requirements:
- Annual penetration testing
- Biannual vulnerability assessments
- Annual security awareness training
- Annual written report to Board or ownership
- Continuous monitoring or quarterly compensating control reviews
How Can a Managed Service Provider Help?
Given the complexity and cost of all this compliance stuff, a lot of dealerships are partnering with specialized IT Managed Service Providers (MSPs) who actually understand automotive industry requirements. Not a bad idea, honestly.
What to look for in an MSP:
- Automotive industry expertise: Not all MSPs understand dealership-specific regulations and systems. You need someone who gets it.
- Compliance credentials: Look for providers with actual experience implementing FTC Safeguards Rule, PCI DSS, and CCPA requirements
- Comprehensive service offerings: Can they handle penetration testing, vulnerability assessments, security awareness training, AND ongoing monitoring?
- Vendor management capabilities: Do they have established relationships with DMS providers and other automotive technology vendors?
- 24/7 security monitoring: Because cyber threats don't take nights and weekends off
Services an MSP can provide:
- Gap analysis and risk assessment
- MFA implementation across all systems
- Encryption deployment
- Annual penetration testing and biannual vulnerability assessments
- Security awareness training and phishing simulations
- Incident response planning and tabletop exercises
- Continuous security monitoring
- Vendor security assessment
- Compliance documentation and "Book of Evidence" maintenance
- FTC breach notification support
Industry Resources and Support
Good news... you're not alone in navigating this compliance maze. Several industry associations provide valuable resources:
National Automobile Dealers Association (NADA)
- Website: nada.org/safeguardsrule
- Resources: Driven Guide for FTC Safeguards Rule compliance, webinars, template policies
- Legal hotline: 800-557-6232
California New Car Dealers Association (CNCDA)
- They've got a 70+ page compliance manual (Version 2, May 2024)
- Sample Information Security Program and Incident Response Plan
- Legal hotline: 916-441-2599
Standards for Technology in Automotive Retail (STAR)
- Website: starstandard.org
- Free risk assessment questionnaire
- Uniform risk assessment standards
The Bottom Line: Compliance Is Business Protection
Look, IT compliance isn't just about avoiding fines. It's about protecting your dealership from business-ending cyberattacks, maintaining customer trust, and ensuring your long-term operational stability.
The CDK Global attack showed us how quickly your entire operation can grind to a complete halt. Honda's $632,500 CCPA fine demonstrated that enforcement is real and active. And with FTC penalties reaching $51,744 per violation... the investment in compliance is really an investment in business continuity.
The dealerships that'll thrive in 2025 and beyond won't be the ones viewing compliance as some annoying burden. They'll be the ones who recognize that robust IT security is actually a competitive advantage and a customer trust builder.
Your next step: Schedule a comprehensive compliance gap analysis to understand exactly where you stand and what you need to implement. Whether you handle compliance in-house or partner with a specialized MSP, the time to act is now. Before the next deadline passes... or worse, before the next breach occurs.
Works Cited
California Privacy Protection Agency. "CPPA Announces First Enforcement Action Against Automotive Company." California Privacy Protection Agency , 12 March 2025, cppa.ca.gov.
CDK Global. "Cybersecurity Insights and Reporting." CDK Global , 2024, cdkglobal.com.
CrowdStrike. "FTC Safeguards Rule Guide for Dealerships." CrowdStrike , 2024, crowdstrike.com.
Federal Trade Commission. "Automobile Dealers & the FTC's Safeguards Rule: Frequently Asked Questions." Federal Trade Commission , 13 May 2024, ftc.gov/business-guidance/resources/automobile-dealers-ftcs-safeguards-rule-frequently-asked-questions.
---. "Standards for Safeguarding Customer Information (Safeguards Rule)." Federal Trade Commission , 9 June 2023, ftc.gov.
Financial Crimes Enforcement Network. "Form 8300 Reporting Requirements." FinCEN , fincen.gov.
National Automobile Dealers Association. "FTC Safeguards Rule Compliance Resources." NADA , 2023, nada.org/safeguardsrule.
PCI Security Standards Council. "PCI Data Security Standard Requirements and Testing Procedures Version 4.0.1." PCI Security Standards Council , March 2024, pcisecuritystandards.org.